Bluetooth is short-range wireless communications technology based on the IEEE 802.15.1 protocol. It works in a crowded license free 2.4 GHz frequency band and shares this resource with many other technologies.
Bluetooth is the optimal solution for establishing small wireless networks called Piconets, by connecting two Bluetooth devices. One of these nodes is Master that can be connected via Bluetooth link to 7 other Bluetooth devices—Slave nodes in Personal Area Network (PAN). Typical data rates are 1-3 Mbps.
The newest versions of Bluetooth is known as Bluetooth Low Energy (BLE) or Bluetooth smart.
It is important to note that Bluetooth and BLE are not compatible technologies. For example, channel bandwidth in Bluetooth technology is 1MHz and in BLE is 2MHz, number of channels in Bluetooth is 79, while BLE supports 40 channels. They also differ in waveforms, transmission power, network organization etc. Bluetooth Versions 4.1/4.2/5.0 support both BLE and Bluetooth standards, but if the master device is a BLE device, the slave must also be a BLE device.
In the most recent Bluetooth Version 5.0 new wave-forms and coding techniques are implemented to achieve longer of 50m or more, less power consumption, lower latency, better robustness and support for a higher number of subscribers in a single Bluetooth network.
At its inception the Bluetooth technology was used for data streaming or file exchange between mobile phones, PCs, printers, headsets, joysticks, mice, keyboards, stereo audio or in the automotive industry.
These days BLE technology became an indispensable protocol used in mobile phones, PCs and other types of devices applicable in gaming, sports, wellness, industrial, medical, home and automation electronics.
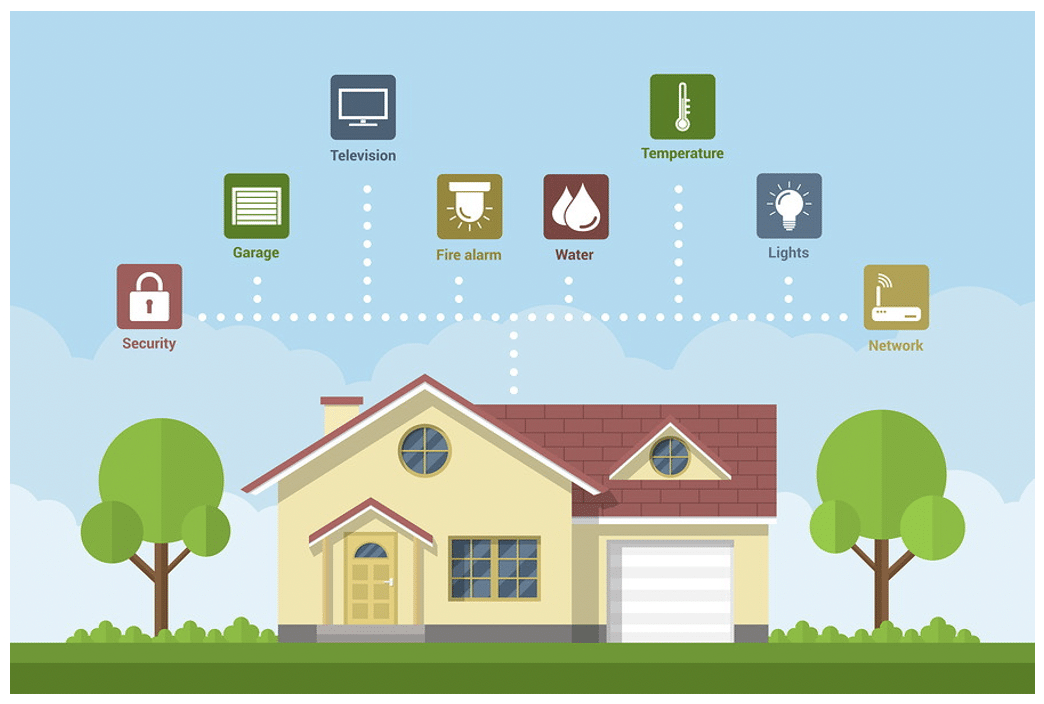
It is an important wireless technology for smart homes and smart buildings, because of the achieved ranges, throughput (2 Mbps), reliability, security performances, low power transmission and low power consumption. BLE provides wireless connectivity that enables home automation via the control of lights—smart bulbs and outlets, smoke detectors, cameras and other security systems, thermostats, video door bells, smart digital locks, hubs and controllers, different assistant devices, universal remotes, gaming consoles, TVs, etc.
In smart buildings, this wireless technology enables automation of some complex systems, as presented in Figure 2, such as: Heating, Ventilation and Air Conditioning (HVAC), lighting, security and indoor positioning.
BLE technology deployed in smart buildings enables optimal space utilization, lowers operating and maintenance costs by condition monitoring via different sensors, contributes to energy savings, enhances the tenants, staff or visitor experiences, etc.
BLE is important for both residential and business buildings. It changes the outlook of the offices by formatting the smart meeting spaces or enabling the sensor-based occupancy mapping, improves workflow efficiency, reduces expenditures, increases revenues and employee satisfaction. In specific smart building types—smart healthcare facilities or smart hospitals, BLE is crucial for patient care and operational efficiency improvements.
In retail industry, coupled with beacon technology, it supports enhanced customer services like in-building or in-store navigation, personalized promotions and specific customer oriented content delivery.
Some BLE limitations for smart home and smart building use cases would be: suitability for short range controls only, interference with other wireless technologies (Wi-Fi, Zigbee, etc.) that are using license free 2.4GHz frequency range, optimal for short-burst wireless communication, lower throughput compared to some other wireless technologies, lack of generic IP connectivity etc.
BLE (Bluetooth) security
Several security modes are recognized in Bluetooth technology. Each version of Bluetooth standard supports some of them. These modes difer based on the point of security initiation in Bluetooth devices. Bluetooth devices must operate in one of four available modes:
- Bluetooth security mode 1 – it is an insecure mode. It is easy to establish wireless connectivity in this mode, but the security is an issue. Bluetooth security mode 1 applicability is in short range devices and only supported up to Bluetooth v2.0 + EDR (Enhanced Data Rate) standard version.
- Bluetooth security mode 2 – a centralized security manager is responsible for access to specific services and devices in this mode, by implementation of the authorization procedure. All Bluetooth devices can support this security mode. However, v2.1 + EDR devices support it only for backward compatibility.
- Bluetooth security mode 3 – in this link level-enforced security mode, the Bluetooth device initiates security procedures before establishment of physical link. It uses authentication and encryption for all connections to and from the device. Bluetooth Security Mode 3 is only supported in Bluetooth devices with v2.0 + EDR or earlier versions.
- Bluetooth security mode 4 – in this mode security procedures are initiated after link setup. Secure Simple Pairing uses Elliptic Curve Diffie Hellman (ECDH) techniques for key exchange and link key generation. This mode was introduced at Bluetooth v2.1 + EDR.
Following five basic security services are implemented in Bluetooth technology:
- Authentication – verifies the identity of devices that are exchanging data, based on their Bluetooth address.
- Confidentiality – ensures that only authorized devices can access and view transmitted data. It is important for preventing compromise of information, for example caused by eavesdropping.
- Authorization – ensures that Bluetooth devices are authorized to use the service.
- Message Integrity – verifies that a message sent is a message received, without any changes in between its source and destination.
- Pairing/Bonding – creates and stores shared secret keys important for a trusted device pair establishment.
Supported security mechanisms developed together with standard versions. In compliance with the Bluetooth Specification Version 5.0, two security modes are implemented in BLE: Security mode 1 and Security mode 2. Within each of them, there are different security layers.
BLE security mode 1 has 4 layers:
- No security (without authentication and without encryption).
- Unauthenticated pairing with encryption (AES-CMAC encryption or AES-128 -is implemented in this layer, during communications when the devices are unpaired).
- Authenticated pairing with encryption.
- Authenticated BLE secure connections pairing with encryption (each time after the pairing is initiated Elliptic Curve Diffie-Helman key agreement protocol is used for key exchange BLE secure connections).
BLE security mode 2 is supported with 2 layers:
- Unauthenticated pairing with data signing.
- Authenticated pairing with data signing.
Security manager protocol, built in the session layer of the OSI reference model, is responsible for pairing, signing between nodes, encryption, key administration, key management, security services management and all other security features in a BLE network.
Bluetooth has some security vulnerabilities, as does any other wireless technologies. Its implementation has to be planned taking into account possible security threats. Some representative security challenges of BLE (Bluetooth) technology are:
- Passive eavesdropping and Man in the Middle (MITM) attacks or identity tracking apply to Bluetooth technology. The interception of radio waves between a smartphone and smart lock can be realized by a different kind of sniffers. Their price range today is 50-100 USD.
- Bluejacking involves the sending of a vCard message via Bluetooth to other Bluetooth users within the short ranges – typically 10 meters. The risk is that the recipient will not realize what the message is and it is possible to open messages automatically, assuming that they are sent from someone known from the contact list.
- Bluebugging is the Bluetooth security issue that allows unauthorized remote access to a phone and usage of its features. It may include placing calls and sending text messages. In the meantime, the owner does not realize that his phone has been taken over. Depending on the attacker’s creativity, denial of service (DoS) attacks and resource misappropriation are consequences of this security issue, too.
- Car Whispering is a hacking technique that implies the usage of specific software to send and receive audio and other files to and from a Bluetooth enabled car stereo system, to invade privacy or listen conversation. It could be applied in the same manner to a Bluetooth enabled systems in smart homes or smart buildings.
- Bluesnipping is a hacking technique capable to extend the range of unauthorized Bluetooth communication system monitoring and provide malicious coverage within a mile distance. It is realized with a specific hardware – a Bluesnipping gun that is made with a few hardware pieces like folding stock, Yagi antenna and Linux terminal.
These vulnerabilities can cause unauthorized access to sensitive information, unauthorized use of Bluetooth devices and other systems or networks to which the Bluetooth devices are connected.
In order to protect a network from security vulnerabilities, it is always useful to be careful with third-party applications and install applications only from trusted sources. Recommendation is to deploy a home network firewall that will protect and encrypt all incoming and outgoing data.
For over 30 years, Marin Ivezic has been protecting people, critical infrastructure, enterprises, and the environment against cyber-caused physical damage. He brings together cybersecurity, cyber-physical systems security, operational resilience, and safety approaches to comprehensively address such cyber-kinetic risk.
Marin leads Industrial and IoT Security and 5G Security at PwC. Previously he held multiple interim CISO and technology leadership roles in Global 2000 companies. He advised over a dozen countries on national-level cybersecurity strategies.